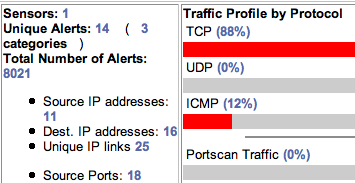
Blast off!
Once your snort.conf file has been configured, you can start running Snort. It can be started with a number of different options that specify everything from output to how it should be run. For now, though, let's just run it with the following command, entered via a Telnet connection into your Snort-enabled system:
snort -D -A full
This command runs it as a background process so that other things can be done and logs full packet information when an alert is generated.
Now that Snort is up and sniffing away at packets, there are many more things you can do to bolster its ability to protect your wireless network. Kismet is a tool similar to Snort that can be deployed as a secondary intrusion detection system. Snort only operates on Layer 3 - the network layer, responsible for IP and other traffic - while Kismet operates on Layer 2 - the datalink layer, responsible for Ethernet frames. So deploying both these programs in tandem can greatly increase the effectiveness of your system.
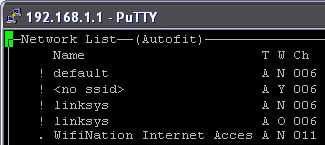
Figure 8: Kismet in action
(Click image to enlarge)
You can also configure Snort to log to a database for easier log analysis. Daniel Walther has written a tutorial on how to do this with MySQL and PostgreSQL. And if you are running Gentoo Linux on your access point machine, this can be taken one step further by including Apache and making the log files web-based. The Gentoo Wiki has a detailed HOWTO for setting this up.