Skill Level 0: Anyone with a wireless computer
It doesn't take special skills to "hack" an unprotected wireless LAN - anyone with a wireless-enabled computer and the ability to turn it on is a potential intruder. Ease of use is often touted as a selling point of wireless networking products, but this often is a double-edged sword. In many cases, people innocently turning on their wireless computers will either automatically connect to your access point or see it in a list of "available" access points.
The following countermeasures should help in securing your network against casual access, but offer no real protection against more skilled intruders. These are listed in relative order of importance. But most of them are so easy to do that I recommend doing them all if your equipment allows.
Countermeasure 1: Change Your Default Settings
At minimum, change the administration password (and username if your equipment allows), and default SSID on your AP or wireless router. Admin passwords for most consumer wireless gear are widely available. So if you don't change yours, you could find yourself locked out of being able to control your own WLAN (until you regain control via a factory reset)!
Changing the default SSID is especially necessary when you are operating in proximity of other APs. If multiple APs from the same manufacturer are in the area, they will have the same SSID and client PCs will have a good chance of "accidentally" connecting to APs other than their own. When you change the SSID, don't use personal information in your SSID! During my Netstumbler sessions, I have seen the following as SSIDs:
- First and Last names
- Street Addresses with apartment numbers
- Social Security Numbers
- Phone Numbers
Changing the default channel of your AP might help you avoid interference from nearby wireless LANs, but it has little value as a security precaution since wireless clients generally automatically scan all available channels for potential connections.
Countermeasure 2: Upgrade Your Firmware, and maybe Hardware
Having the most current firmware installed on your AP can sometimes help improve security. Updated firmware often includes security bug fixes and sometimes adds new security features. With some newer consumer APs, a single click will check for and install new firmware. This is in contrast to older APs which required the user to look up, download and install the latest firmware from a sometimes difficult-to-navigate support site.
APs that are more than a few years old have often reached their end of support lifecycle, meaning that no new firmware upgrades will be made available. If you find that your AP's latest firmware doesn't support at least the improved security of WPA (Wi-Fi Protected Access), and preferably the latest version called WPA2, you should seriously consider upgrading to new gear. The same goes for your wireless clients!
Virtually all currently-available 802.11g gear supports at least WPA and is technically capable of being upgraded to WPA2. But manufacturers are not always diligent in their support of older products, so if you want to be sure that your gear supports WPA2, either check the Wi-Fi Alliance's certification database, or do some Googling in both the Web and Groups.
Countermeasure 3: Disable SSID broadcast
Most APs allow users to disable SSID broadcasting, which will thwart a Netstumbler scan. This will also stop Windows XP users using XP's built-in Wireless Zero Configuration utility and other client applications from initially seeing the wireless network. Figure 1 shows the control labeled "Hide ESSID" that will do the trick on a ParkerVision access point. ("SSID" and "ESSID" both refer to the same thing.)
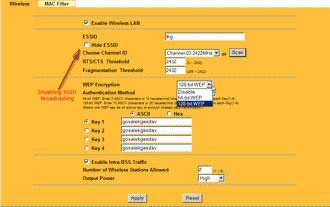
Figure 1: Disabling SSID Broadcast on a Parkervision AP
(click image to enlarge)
NOTE: Disabling SSID broadcast will not prevent a potential intruder using Kismet or other wireless survey tools such as AirMagnet from seeing your wireless network. These tools don't rely on SSID broadcast for available network detection.