Skill Level 1: Anyone with commonly available wardriving tools
Now let's move up a notch on skill level to that of your common "wardriver", who actively cruises around looking for wireless LANs. Some people wardrive for kicks to see how many wireless networks they can detect and never attempt to use the vulnerable networks they find. But others are not so benign in their intent and do connect, use and sometimes abuse unsuspecting wireless LAN owners.
At Skill Level 1, I'll assume that all the countermeasures suggested for Skill Level 0 do not work and the potential intruder can see your wireless network. The only effective countermeasures at this point involve encryption and authentication. I'll save authentication for later and focus on encryption.
NOTE: While forcing all wireless traffic to use a VPN (Virtual Private Network) is one solution, VPN's are notoriously difficult to set up and beyond the scope of this article.
Countermeasure 7: Encryption
Wireless LAN owners should run the strongest type of encryption available to them. Your choices will be dictated by the capabilities of your WLAN hardware and your options are WEP, WPA and WPA2.
WEP (Wireless Equivalent Privacy) is the weakest wireless security technology, but currently the most widely deployed due to its availability on virtually all 802.11 wireless products. You may have to use it because many consumer wireless product manufacturers have opted to not provide upgrades from WEP to WPA for 802.11b products. And others are still creating new products such as some VoIP wireless phones that support only WEP, forcing some WLAN owners to downgrade their security to accomodate the lowest common level of security.
Either WPA (Wi-Fi Protected Access) or WPA2 provide adequate wireless security, due to their stronger encryption technology and improved key management. The main difference between the two is that WPA2 supports stronger AES (Advanced Encryption Standard) encryption. But to further confuse users, there are some WPA-labeled products that allow the selection of AES vs. the WPA-standard TKIP encryption.
Most 802.11g products support WPA (but there are exceptions), but upgrades to WPA2 for older products are still in the process of being rolled out - even though the 802.11i standard that WPA2 is based on was ratified in June 2004.
I recommend that you use WPA as a minimum. It is as effective as WPA2 and, at least as I write this, more widely supported. Implementing this recommendation, however, may require purchasing new equipment, especially if you currently are using 802.11b in your WLAN. But standard 11g gear is relatively inexpensive and could be the best security investment you make.
Most consumer APs support only the "Personal" version of WPA or WPA2, which is also referred to as WPA-PSK (Pre-Shared Key) (see Figure 4). WPA2 or WPA "Enterprise" (also known as WPA "RADIUS") is also supported by some consumer wireless gear, but is of little use without the additional RADIUS server required to implement it.
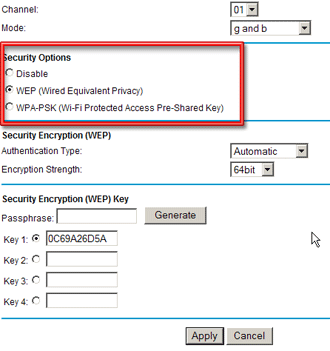
Figure 4: Encrypting traffic on a Netgear AP
For most personal WLANs, using WPA-PSK will provide adequate protection, but it is essential to use a key that is sufficiently long and random. Do not use a number, or a word from the dictionary, since programs such as cowpatty are already available to perform dictionary-based attacks against WPA-PSK.
Robert Moskowitz, Senior Technical Director ICSA Labs, recommended in this article using an 128 bit PSK. Fortunately, all WPA implementations accept alphanumeric PSKs, which would require only 16 characters to implement Mr. Moskowitz' recommendation.
There are many password generators available on the Internet that can be found by a quick search. This one has lots of bells and whistles and even provides an estimation of how long it would take to crack the password it generates.
As a final note, some manufacturers have started selling APs and wireless cards that promise "one touch" easy setup of secured wireless connections. Buffalo Technology had the first products based on their AOSS (AirStation One-Touch Secure Station) technology. Linksys has recently starting selling products based on similar technology from Broadcom dubbed SecureEasySetup. You can read a comparative review of these two technolgies here.