Setting it all up
We've had a quick look at the structure of a network where the Captive Portal may be useful and how it will allow us to control access to the Internet. Let's now look at the detail of getting it configured and running.
The basics of m0n0wall were covered in my previous article covering v1.0 of the software. If you are new to m0n0wall, this covers hardware installation and getting m0n0wall up and running. The set up process below assumes you already have a version of m0n0wall v1.1 running on either a standalone PC or one of the embedded PC platforms I discussed in my m0n0wall review.
The steps are:
- Configure the PORTAL network interface
- Configure DHCP to hand out a suitable IP configuration to clients (PCs and other devices)
- Configure the Captive Portal itself, connection time-outs etc.
- Upload the HTML for the portal page
Step 1: Configure the PORTAL network interface
m0n0wall requires a minimum of two physical network interfaces for the LAN and WAN. You could run the captive portal on the LAN interface, however this would allow anonymous users access to any of your PCs/Servers on the LAN as well as your Internet connection unless you connected those users via a VLAN-capable switch.
A more secure method is to put the Captive Portal on a separate interface in the same way as it is good practice to put Internet-facing servers on a separate interface, normally referred to as a DMZ (demilitarised zone). As I pointed out previously, this has the benefit of letting you establish separate firewall rules for the two classes of users.
m0n0wall handles additional network interfaces as Optional interfaces. In my case, I'm using a PC Engines WRAP, so I have a third physical Ethernet interface that I am going to use for the Captive Portal. As you can see in Figure 2, m0n0wall allows you to rename the interface for ease of identification.
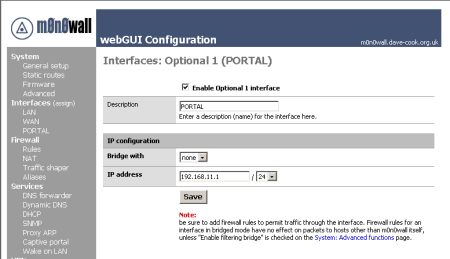
Figure 2: Configuring the PORTAL interface
(click on the image for a larger view)
Note that the network address / subnet used isn't too important as long as it is not the same as your LAN and either:
- a private network that meets RFC 1918 (10/8, 172.16/12, 192.168/16), typically a network between 192.168.1.0/24 and 192.168.254.0/24
or - a subnet of public IP addresses assigned by your ISP and routed to your m0n0wall
I used 192.168.11.0/24 (subnet mask 255.255.255.0) which allows 254 valid IP addresses. Of those I have assigned:
- 192.168.11.1 to the Portal interface of m0n0wall
- 192.168.11.2 to the wireless AP
To provide wireless access, I am going to use a stand-alone access point instead of trying to use m0n0wall's built-in wireless support. This lets us use any off-the-shelf access point instead of limiting us to the relatively small set of WLAN chipsets supported by m0n0wall (and FreeBSD). It also frees us from having to use a mini-PCI WLAN card with either the Soekris or PCEngines WRAP embedded platforms or having to add a PC Card / CardBus adapter so that we can use a CardBus WLAN card with a desktop.
I used a BuffaloTech WLA-G54C-1 G54 Compact Access Point while writing this article. It's relatively inexpensive (I paid around $74) and supports both 802.11b and 802.11g standards. For more details, please have a look at Tim Higgins' review. Since I didn't have a cross-over cable handy, I simply plugged the Portal interface of the WRAP and the AP into a 10mbps hub.
I won't be covering the configuration of the AP itself in this article, since that's adequately covered by your AP's user manual and there is nothing in particular that needs to be set for use with the m0n0wall Captive Portal.