Network Recon with Kismet
You're now ready to start Kismet, which is a Linux-based wireless scanner. It's a handy tool for surveying the wireless airwaves around you to find target wireless LANs to crack. Kismet also captures traffic, but there are other tools such as airodump (part of Aircrack) that do a better job in the context of cracking WEP. So we'll be using it to make sure our wireless card is working and for scanning for wireless networks. Then we will switch to different tools in Part 2 to actually sniff and capture traffic.
You get to Kismet by clicking on the Programs icon, then Auditor, then Wireless, then Scanner/Analyzer, and finally Kismet (Figure 13).
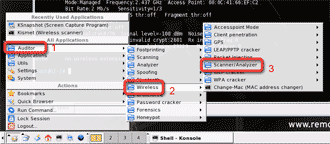
Figure 13: Getting to Kismet
(click image to enlarge)
In addition to scanning wireless networks, Kismet captures packets into a file for later analysis. So Kismet will ask for the directory to save the captured files in. Click Desktop and then OK (Figure 14).
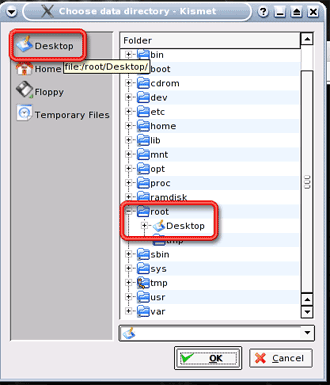
Figure 14: Specifying the Save Location
Kismet will then ask for a prefix for the captured files (Figure 15). Change the default name to capture and then click OK.
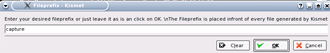
Figure 15: Specifying the file prefix
(click image to enlarge)
As Kismet starts, it will display all the wireless networks in range (Figure 16), which should hopefully include the target WLAN you set up. The channel number, under the Ch column, should match what you have written down. If Kismet has found many nearby access points, you may want to move the lab farther away from the Access Points, or disconnect any high-gain antennas you have connected.
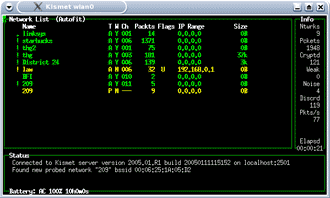
Figure 16: Kismet at work
(click image to enlarge)
While Kismet is jumping through all the channels and SSIDs looking for interesting information, you will see the number of packets changing for all the access points. In the column at the right side of the screen, Kismet displays the total number of networks found, the number of packets captured and the number of encrypted packets seen.
Even with the target computer off, Kismet is detecting packets from our AP. This is because APs send out "beacons", which tell wireless computers that an AP is in range. You can think of it as the AP announcing, "My name is XXXXX, please connect to me."