Security
The 7130 was one of the first to support Wi-Fi Protected Access (WPA) for improved WLAN security. Figure 4 shows the WPA "Enterprise" mode setup, which requires using an external RADIUS server.
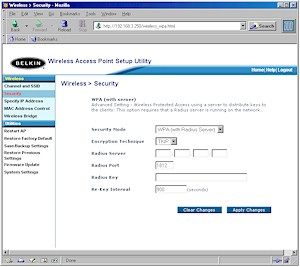
Figure 4: WPA settings
(click on the image for a full-sized view)
The 7130 also supports WPA's "SOHO" mode, which is also known as WPA-PSK (Pre-Shared Key). I didn't show this screen because all it has is an entry box for the 8 to 63 character key and a selector for Encryption method.
The encryption method selector is actually due to Broadcom's choice of providing access to its hardware-based AES (Advanced Encryption Standard) encryption in addition to the TKIP encryption that is mandatory for all WPA implementations. AES is part of the full 802.11i (now known as WPA2) spec, but wasn't included in WPA because its processing requirements would have killed the throughput of "legacy" 11b adapters that don't have hardware AES encryption processors.
The 7130 also supports 64 and 128 bit WEP encryption if your wireless client's WPA driver update isn't yet available. But if you're using any of Belkin's 54g clients, forget about WEP and use WPA - it's easier and more secure.
If you're looking for the "Advanced" wireless settings typically found on other AP's, don't bother. This means that you can't set Authentication Type, Beacon & DTIM Intervals, or RTS & Fragmentation Thresholds, nor can you adjust Transmit Power. These features probably won't be missed by most home networkers, but sophisticated users might wish they were available.
Wrapping up the 7130's security features is its Filtered MAC Address control. You can enter a list of client MAC addresses, which can all be either permitted or denied association with the AP. But the list can't be saved or loaded to / from a file, and you aren't given a pick-list of associated or in-range clients to ease the chore of creating your list.