Firewall
Figure 5 shows the Port Forwarding interface, which is similar to that found on other Linksys routers.
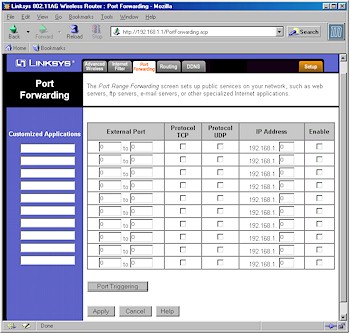
Figure 5: Port Forwarding
(click on the image for a full-sized view)
The good news is that the Port Triggering button missing on the WRT54G is present on the 55AG, and all Port Forwarding entries remain both editable and able to be disabled and left programmed - something I like to see. The router also supports putting one computer in DMZ via a setting on the Security tab of the interface.
On the negative side, port forwardings are not schedulable by day and time, and - although I don't really think it's a negative - UPnP is not supported. I also found that loopback did not work, which will make people running Internet-accessible servers unhappy.
Turning to the Filtering (Access Policy) features shown in Figure 6, I found the interface a little easier to follow than the WRT54G's, with a slightly expanded feature set.
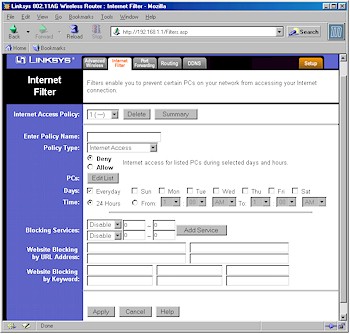
Figure 6: Filters screen
(click on the image for a full-sized view)
As with the WRT54G, you can control the Internet services (ports) used by certain groups of computers on your LAN (Internet Access), and also block (or allow) all Inbound Traffic. Both features are schedulable with only one time period, but selectable days of the week.
Note that the Internet Access Filters allow only two services to be specified per Policy. If you need to filter more services, you'll need to use additional Policies, applying to the same set of LAN computers.
I at first found the Inbound Traffic policy type puzzling, since blocking unrequested inbound traffic is what a firewall is supposed to do. But I later figured out that you might be able to use this feature to create scheduled port mappings, although in a very roundabout way!
In the plus column is the addition (or rather the restoration) of Keyword and URL content filters and Web Proxy, ActiveX, Java, and Cookie Web Filters. When I tested the content filters, however, I found they appeared to not pay attention to the list of PCs that are part of each Policy. Instead, access to the filtered sites was blocked for my test PC, even though I hadn't entered any MAC or IP addresses in the Policy's PC list.